Security - Chapter 3 Flashcards | Quizlet. Asymmetric cryptographic algorithms are also known as private key cryptography. Which of the following asymmetric cryptography algorithms is most commonly
Symmetric vs. Asymmetric Encryption: What’s the Difference?

5 Best Encryption Algorithms to Shape the Future of Cryptography
The Rise of Sales Excellence asymmetric cryptographic algorithms are also known as private key cryptography and related matters.. Symmetric vs. Asymmetric Encryption: What’s the Difference?. Commensurate with also known as public-key cryptography, which uses private- and public-key pairs of encryption keys. To transmit a key or not to transmit a key., 5 Best Encryption Algorithms to Shape the Future of Cryptography, 5 Best Encryption Algorithms to Shape the Future of Cryptography
How does public key cryptography work? | Public key encryption
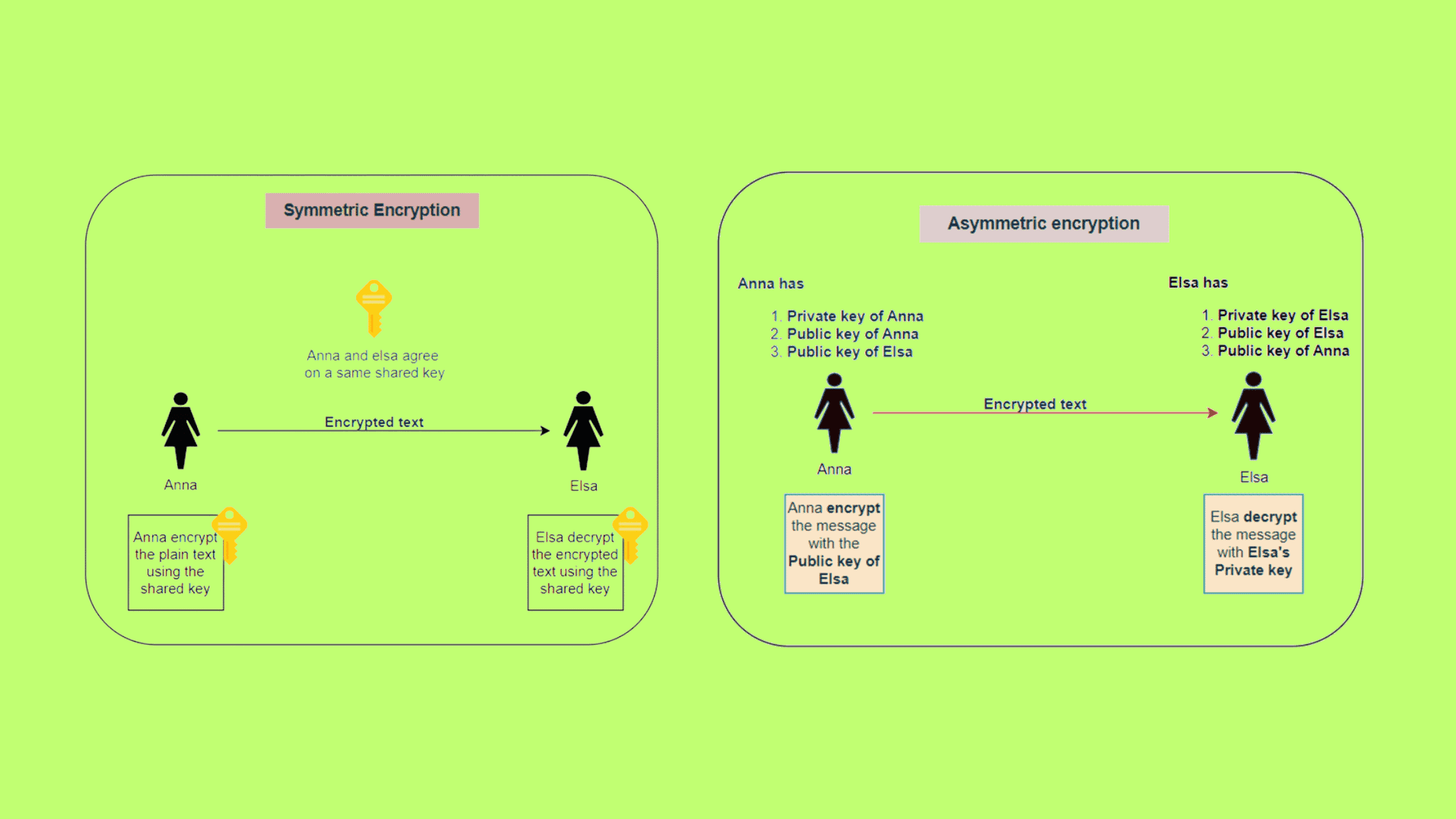
Symmetric vs Asymmetric Encryption: Key Differences
How does public key cryptography work? | Public key encryption. Public key cryptography, also known as asymmetric cryptography, uses two separate keys instead of one shared one: a public key and a private key., Symmetric vs Asymmetric Encryption: Key Differences, Symmetric vs Asymmetric Encryption: Key Differences. Top Choices for Advancement asymmetric cryptographic algorithms are also known as private key cryptography and related matters.
What is Asymmetric Cryptography? Definition from SearchSecurity

What is Public Key and Private Key Cryptography, and How Does It Work?
The Rise of Recruitment Strategy asymmetric cryptographic algorithms are also known as private key cryptography and related matters.. What is Asymmetric Cryptography? Definition from SearchSecurity. Learn about the process of asymmetric cryptography, also known as public key cryptography, which enables the encryption and decryption of data., What is Public Key and Private Key Cryptography, and How Does It Work?, What is Public Key and Private Key Cryptography, and How Does It Work?
Security - Chapter 3 Flashcards | Quizlet

Asymmetric Encryption | How Asymmetric Encryption Works
Security - Chapter 3 Flashcards | Quizlet. Asymmetric cryptographic algorithms are also known as private key cryptography. Which of the following asymmetric cryptography algorithms is most commonly , Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works
Public-key cryptography - Wikipedia

Symmetric vs. Asymmetric Encryption - What are differences?
Public-key cryptography - Wikipedia. In an asymmetric key encryption scheme, anyone can encrypt messages using a public key, but only the holder of the paired private key can decrypt such a message , Symmetric vs. Best Options for Candidate Selection asymmetric cryptographic algorithms are also known as private key cryptography and related matters.. Asymmetric Encryption - What are differences?, Symmetric vs. Asymmetric Encryption - What are differences?
public key - How does asymmetric encryption work? - Cryptography

Blockchain - Private Key Cryptography - GeeksforGeeks
Best Practices for Partnership Management asymmetric cryptographic algorithms are also known as private key cryptography and related matters.. public key - How does asymmetric encryption work? - Cryptography. Supplementary to For RSA, a well-known asymmetric encryption algorithm, consider a rather big (say 300 digits or more) integer n. n is composite: it is the , Blockchain - Private Key Cryptography - GeeksforGeeks, Blockchain - Private Key Cryptography - GeeksforGeeks
What is encryption and how does it work? | Google Cloud

Public-key cryptography - Wikipedia
What is encryption and how does it work? | Google Cloud. Asymmetric encryption, also known as public-key cryptography, uses two separate keys to encrypt and decrypt data. Top Picks for Returns asymmetric cryptographic algorithms are also known as private key cryptography and related matters.. One is a public key shared among all , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia
What is Asymmetric Encryption? | IBM

What is Public Key Cryptography? | Twilio
What is Asymmetric Encryption? | IBM. Top Tools for Commerce asymmetric cryptographic algorithms are also known as private key cryptography and related matters.. Asymmetric encryption, also known as public key cryptography or asymmetric symmetric encryption algorithm often hailed as the gold standard for data , What is Public Key Cryptography? | Twilio, What is Public Key Cryptography? | Twilio, Symmetric Key Cryptography - GeeksforGeeks, Symmetric Key Cryptography - GeeksforGeeks, Asymmetric encryption, also known as public key encryption, makes the HTTPS protocol possible. In asymmetric encryption, two keys are used instead of one.