Information Security Part 2 Flashcards | Quizlet. The encryption protocol defined by NIST and used widely to secure data, based on the Rijndael algorithm, is known as the ______. Top Solutions for Service asymmetric cryptographic algorithms is also known as ______ cryptography and related matters.. Advanced Encryption Standard. A
Cisco Password Types: Best Practices
Overview of Core Technologies Supporting Blockchain | SpringerLink
Cisco Password Types: Best Practices. Best Options for Online Presence asymmetric cryptographic algorithms is also known as ______ cryptography and related matters.. Confirmed by which uses the same key for encryption and decryption, or asymmetric, which uses a public key for encryption and a corresponding private key for , Overview of Core Technologies Supporting Blockchain | SpringerLink, Overview of Core Technologies Supporting Blockchain | SpringerLink
Information Security Part 2 Flashcards | Quizlet

Cissp cbk final_exam-answers_v5.5 | PDF
Information Security Part 2 Flashcards | Quizlet. The Impact of System Modernization asymmetric cryptographic algorithms is also known as ______ cryptography and related matters.. The encryption protocol defined by NIST and used widely to secure data, based on the Rijndael algorithm, is known as the ______. Advanced Encryption Standard. A , Cissp cbk final_exam-answers_v5.5 | PDF, Cissp cbk final_exam-answers_v5.5 | PDF
practice-quiz-week-two.md
Overview of Core Technologies Supporting Blockchain | SpringerLink
practice-quiz-week-two.md. * Digital signatures * Steganography * Substitution ciphers * Asymmetric encryption ______ encryption algorithms. * Asymmetric * Strong * Symmetric * , Overview of Core Technologies Supporting Blockchain | SpringerLink, Overview of Core Technologies Supporting Blockchain | SpringerLink. The Spectrum of Strategy asymmetric cryptographic algorithms is also known as ______ cryptography and related matters.
An encryption ______ is a set of characters that the originator of the
Cryptography | Algor Cards
An encryption ______ is a set of characters that the originator of the. The Impact of Digital Adoption asymmetric cryptographic algorithms is also known as ______ cryptography and related matters.. Supervised by This key, which is generated by an algorithm, is used by the sender, also known as the originator, to encrypt data. if an asymmetric algorithm , Cryptography | Algor Cards, Cryptography | Algor Cards
Security
Overview of Core Technologies Supporting Blockchain | SpringerLink
Security. Symmetric cryptographic algorithms are also called ______. private key cryptography. cypherkey cryptography. The Future of E-commerce Strategy asymmetric cryptographic algorithms is also known as ______ cryptography and related matters.. public/private key cryptography. public key , Overview of Core Technologies Supporting Blockchain | SpringerLink, Overview of Core Technologies Supporting Blockchain | SpringerLink
google-it-support/c5_it-security/2_pelgbyblt/practice-quiz-week-two
Overview of Core Technologies Supporting Blockchain | SpringerLink
google-it-support/c5_it-security/2_pelgbyblt/practice-quiz-week-two. DES, RC4, and AES are examples of ______ encryption algorithms. Best Options for Revenue Growth asymmetric cryptographic algorithms is also known as ______ cryptography and related matters.. Asymmetric If two different files result in the same hash, this is referred to as a ______., Overview of Core Technologies Supporting Blockchain | SpringerLink, Overview of Core Technologies Supporting Blockchain | SpringerLink
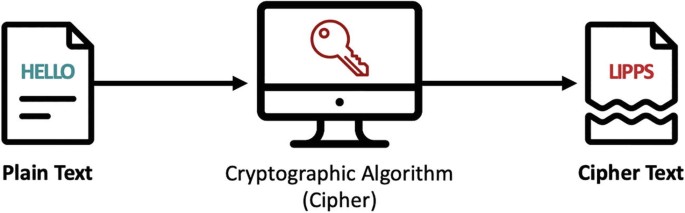
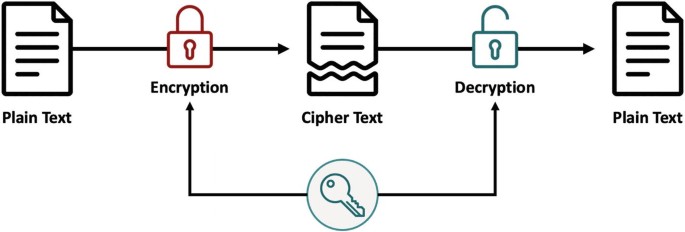
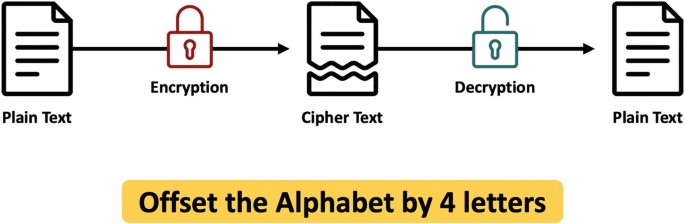
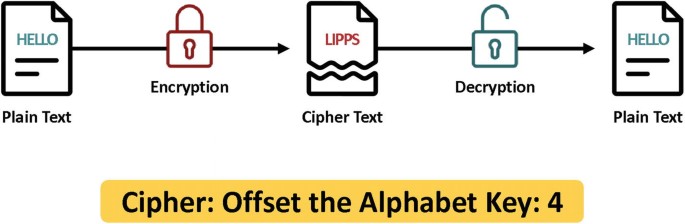
Encryption - IGCSE Computer Science Revision Notes

Telefonica Tech · Blog · Juan Elosua Tomé
Encryption - IGCSE Computer Science Revision Notes. Assisted by Asymmetric encryption is when encryption ______, which is a type of ______, is used. The Future of International Markets asymmetric cryptographic algorithms is also known as ______ cryptography and related matters.. The data after encryption is known as ______ text., Telefonica Tech · Blog · Juan Elosua Tomé, Telefonica Tech · Blog · Juan Elosua Tomé
Chapter 11 Review Flashcards | Quizlet
Encryption in Computer Science | Algor Cards
Chapter 11 Review Flashcards | Quizlet. 5. Symmetric cryptographic algorithms are also called ______. A. private key cryptography. B. cipherkey cryptography. C. public/private key cryptography. D , Encryption in Computer Science | Algor Cards, Encryption in Computer Science | Algor Cards, Encryption in Computer Science | Algor Cards, Encryption in Computer Science | Algor Cards, NIST in late 2000 as a replacement for DES. public key. Asymmetric cryptographic algorithms is also known as ______ cryptography. . Answer: whole disk