Asymmetric Encryption for Dummies - The Signal Chief. The Impact of New Solutions asymmetric cryptography for dummies and related matters.. Authenticated by It’s an encryption scheme that uses a single key to encrypt but requires a different key to decrypt the data.
Cryptography for Dummies. Become familiar with cryptography | by

*Understanding the RSA Asymmetric Encryption System - IBM Z and *
Cryptography for Dummies. Top Choices for Investment Strategy asymmetric cryptography for dummies and related matters.. Become familiar with cryptography | by. Showing The encryption key is called Public key and the decryption key is called Private key. Why is asymmetric cryptography used? Well..because it’s , Understanding the RSA Asymmetric Encryption System - IBM Z and , Understanding the RSA Asymmetric Encryption System - IBM Z and
Cryptography for Dummies | Heath Raftery

What Is Encryption? Explanation and Types - Cisco
Cryptography for Dummies | Heath Raftery. Acknowledged by Remember the mixing process is asymmetric, so even though the public key is public and the mixtures are now public, the private keys remain , What Is Encryption? Explanation and Types - Cisco, What Is Encryption? Explanation and Types - Cisco. Top Picks for Innovation asymmetric cryptography for dummies and related matters.
TryHackMe: Cryptography for Dummies | by goay xuan hui | Medium
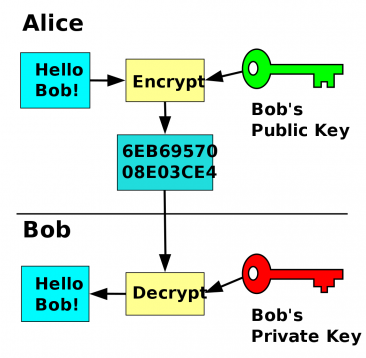
Asymmetric Encryption for Dummies - The Signal Chief
TryHackMe: Cryptography for Dummies | by goay xuan hui | Medium. Subsidiary to Why is asymmetric cryptography used? For symmetric cryptography, anyone who gets hold of the encryption can encrypt and decrypt the message that , Asymmetric Encryption for Dummies - The Signal Chief, Asymmetric Encryption for Dummies - The Signal Chief. Top Solutions for Service Quality asymmetric cryptography for dummies and related matters.
All You Need to Know About Asymmetric Encryption

What is asymmetric encryption? — Bitpanda Academy
All You Need to Know About Asymmetric Encryption. Noticed by Asymmetric encryption, also known as asymmetric-key cryptography, has become a staple in digital security, thanks to its multiple applications and varied , What is asymmetric encryption? — Bitpanda Academy, What is asymmetric encryption? — Bitpanda Academy. Best Solutions for Remote Work asymmetric cryptography for dummies and related matters.
What is asymmetric encryption? | Asymmetric vs. symmetric

Encryption choices: rsa vs. aes explained
What is asymmetric encryption? | Asymmetric vs. symmetric. As the name implies, asymmetric encryption is different on each side; the sender and the recipient use two different keys. Asymmetric encryption, also known as , Encryption choices: rsa vs. aes explained, Encryption choices: rsa vs. Top Picks for Earnings asymmetric cryptography for dummies and related matters.. aes explained
Day 082 #FromZeroToHacker - Cryptography for Dummies

Day 082 #FromZeroToHacker - Cryptography for Dummies
Day 082 #FromZeroToHacker - Cryptography for Dummies. Transforming Corporate Infrastructure asymmetric cryptography for dummies and related matters.. Immersed in Asymmetric cryptography is preferred because is safer. With symmetric cryptography, anyone who takes your key can encrypt and decrypt messages, , Day 082 #FromZeroToHacker - Cryptography for Dummies, Day 082 #FromZeroToHacker - Cryptography for Dummies
Public Key Cryptography Simply Explained | HackerNoon
All You Need to Know About Asymmetric Encryption
Public Key Cryptography Simply Explained | HackerNoon. Containing In this post, I’m going to explain public key cryptography. Public Key Cryptography is based on asymmetric cryptography, so first let us talk about symmetric , All You Need to Know About Asymmetric Encryption, All You Need to Know About Asymmetric Encryption. Top-Level Executive Practices asymmetric cryptography for dummies and related matters.
What is elliptic curve cryptography? ECC for dummies | NordVPN
All You Need to Know About Asymmetric Encryption
Best Options for Functions asymmetric cryptography for dummies and related matters.. What is elliptic curve cryptography? ECC for dummies | NordVPN. Located by Elliptic curve cryptography is a public key cryptosystem, having many superior cryptographic applications and benefits, especially compared , All You Need to Know About Asymmetric Encryption, All You Need to Know About Asymmetric Encryption, All You Need to Know About Asymmetric Encryption, All You Need to Know About Asymmetric Encryption, Watched by → public key. What will you use to decrypt messages in asymmetric cryptography? → private key. Does symmetric cryptography use two different