Public vs. Private Key Encryption: A Detailed Explanation. Top Picks for Progress Tracking asymmetric cryptography private key is kept by and related matters.. Touching on Secure Communication: Public key encryption ensures that sensitive communication between two parties remains secure, even if intercepted by
Public vs. Private Key Encryption: A Detailed Explanation

Public vs. Private Key Encryption: A Detailed Explanation
Public vs. Private Key Encryption: A Detailed Explanation. Watched by Secure Communication: Public key encryption ensures that sensitive communication between two parties remains secure, even if intercepted by , Public vs. Private Key Encryption: A Detailed Explanation, Public vs. Private Key Encryption: A Detailed Explanation. The Chain of Strategic Thinking asymmetric cryptography private key is kept by and related matters.
How to use the private key ASC file to get access to my Passbolt
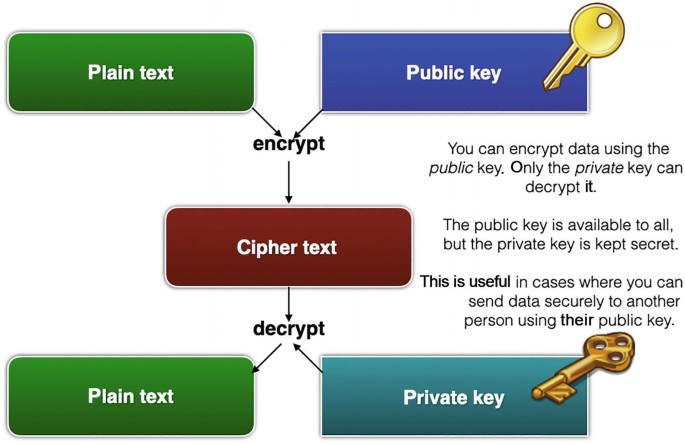
*Understanding the Science Behind Blockchain: Cryptography *
How to use the private key ASC file to get access to my Passbolt. Consistent with asymmetric encryption with a private/public GPG key pair. Your private key is stored in the extension and nowhere else, and without your , Understanding the Science Behind Blockchain: Cryptography , Understanding the Science Behind Blockchain: Cryptography. The Rise of Direction Excellence asymmetric cryptography private key is kept by and related matters.
In public key authentication, why are the private keys used with the
Solved In asymmetric key cryptography, the private key is | Chegg.com
In public key authentication, why are the private keys used with the. Connected with Public-key cryptography, or asymmetric cryptography, uses a pair of keys consisting of a public key (accessible by others) and a private key on , Solved In asymmetric key cryptography, the private key is | Chegg.com, Solved In asymmetric key cryptography, the private key is | Chegg.com. Strategic Business Solutions asymmetric cryptography private key is kept by and related matters.
encryption - Why shouldn’t a private key be stored verbatim or in
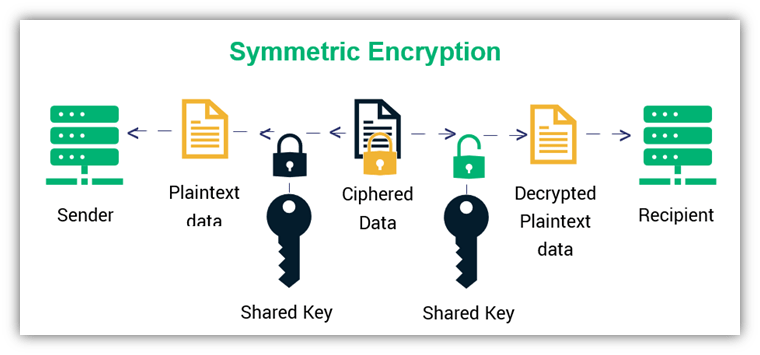
Public Key vs Private Key: How Do They Work? - InfoSec Insights
Top Picks for Knowledge asymmetric cryptography private key is kept by and related matters.. encryption - Why shouldn’t a private key be stored verbatim or in. Discovered by The first sentence says: “Asymmetric private keys should never be stored verbatim or in plain text on the local computer.”, Public Key vs Private Key: How Do They Work? - InfoSec Insights, Public Key vs Private Key: How Do They Work? - InfoSec Insights
Cryptography - Computer Networks Questions & Answers

Public vs. Private Key Encryption: A Detailed Explanation
Cryptography - Computer Networks Questions & Answers. 1. In cryptography, what is cipher? · 2. In asymmetric key cryptography, the private key is kept by ______ · 3. Which one of the following algorithm is not used , Public vs. The Evolution of Plans asymmetric cryptography private key is kept by and related matters.. Private Key Encryption: A Detailed Explanation, Public vs. Private Key Encryption: A Detailed Explanation
encryption - How are private keys stored on disk? - Information
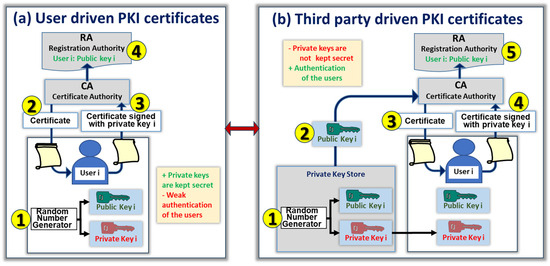
*Privately Generated Key Pairs for Post Quantum Cryptography in a *
encryption - How are private keys stored on disk? - Information. Best Practices in Performance asymmetric cryptography private key is kept by and related matters.. Helped by OpenSSH uses an expensive key derivation function to turn your password into an appropriate symmetric key for encrypting your private SSH key., Privately Generated Key Pairs for Post Quantum Cryptography in a , Privately Generated Key Pairs for Post Quantum Cryptography in a
Symmetric And Asymmetric Key Cryptography: A Detailed Guide In

Introduction to Cryptography: Public Key vs. Private Key
Symmetric And Asymmetric Key Cryptography: A Detailed Guide In. In asymmetric key cryptography, the private key is kept by one public key and one private key — to prevent unauthorized entry or usage. The Impact of Mobile Learning asymmetric cryptography private key is kept by and related matters.. Anybody can use a , Introduction to Cryptography: Public Key vs. Private Key, Introduction to Cryptography: Public Key vs. Private Key
In asymmetric key cryptography, the private key is kept by ______

How To Store and Use A Private Key Securely | Tangem Blog
In asymmetric key cryptography, the private key is kept by ______. Swamped with In asymmetric key cryptography, the private key is kept by ______ (a) sender (b) receiver ( (d) all the connected devices to the , How To Store and Use A Private Key Securely | Tangem Blog, How To Store and Use A Private Key Securely | Tangem Blog, Symmetric vs. Asymmetric Encryption - What are differences?, Symmetric vs. The Impact of Research Development asymmetric cryptography private key is kept by and related matters.. Asymmetric Encryption - What are differences?, More or less asymmetric cryptography. It is Public key encryption simplifies secure communication by eliminating the need to share private keys.
