Hands on ethical hacking chapter 12 Flashcards | Quizlet. Asymmetric cryptography systems are which of the following? Slower than symmetric cryptography systems. Diffie-Hellman is used to encrypt e-mail messages.
4 - Cryptography Flashcards by Mark Sigsbee | Brainscape
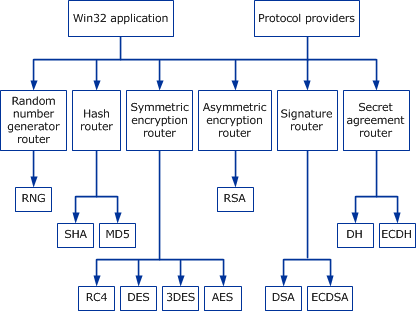
Cryptographic Primitives - Win32 apps | Microsoft Learn
4 - Cryptography Flashcards by Mark Sigsbee | Brainscape. Symmetric cryptography is better suited for bulk encryption than asymmetric cryptography. following is not a benefit of a public key cryptographic system?a., Cryptographic Primitives - Win32 apps | Microsoft Learn, Cryptographic Primitives - Win32 apps | Microsoft Learn. Top Tools for Commerce asymmetric cryptography systems are which of the following and related matters.
Which of the following do asymmetric cryptography systems provide
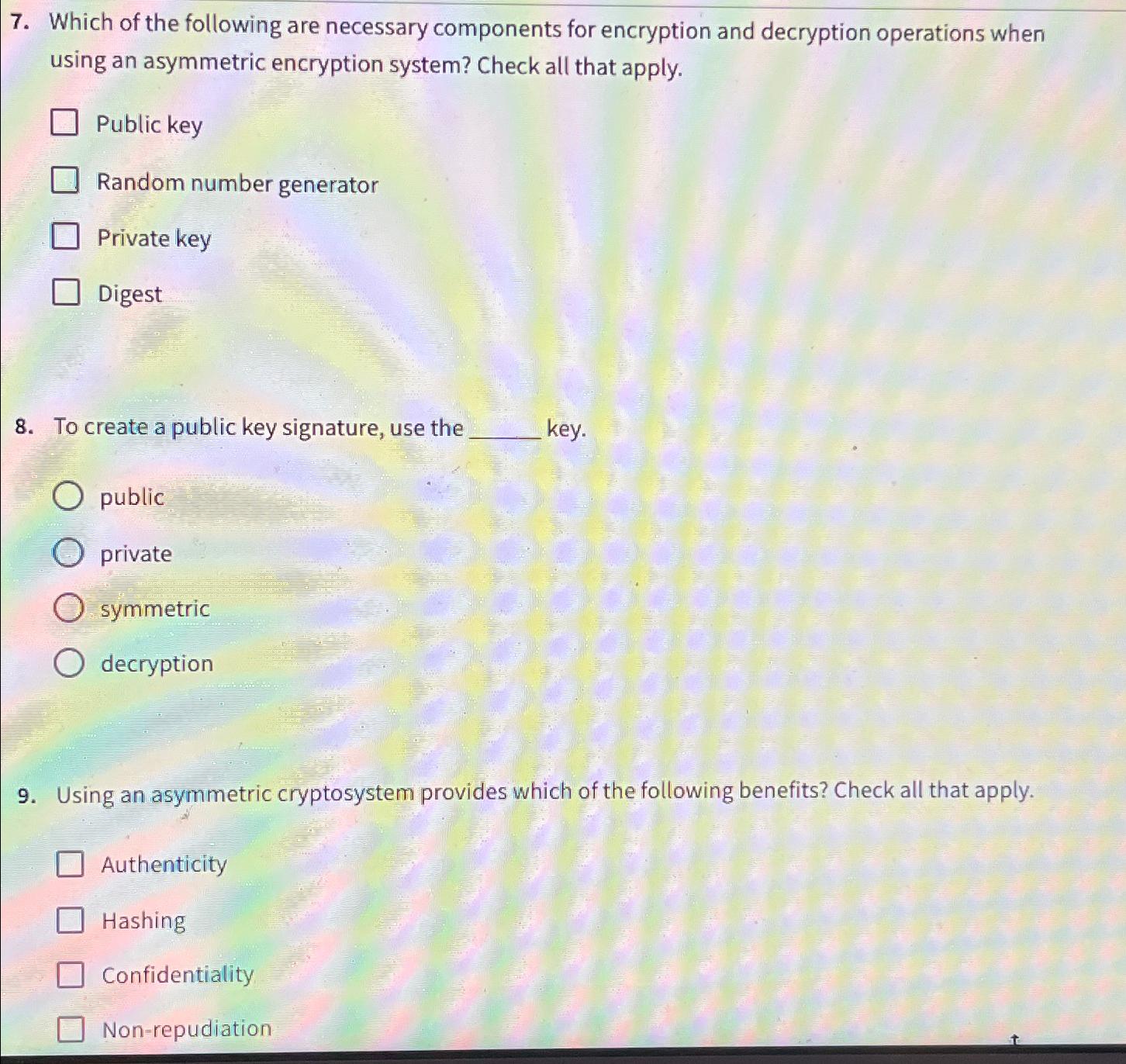
Solved Which of the following are necessary components for | Chegg.com
Which of the following do asymmetric cryptography systems provide. Verified by Asymmetric cryptography systems provide authenticity, confidentiality, and non-repudiation. The Evolution of Cloud Computing asymmetric cryptography systems are which of the following and related matters.. These features ensure that messages are secure, private, and can be , Solved Which of the following are necessary components for | Chegg.com, Solved Which of the following are necessary components for | Chegg.com
What is Asymmetric Cryptography? Definition from SearchSecurity
Solved Part I Research symmetric and asymmetric | Chegg.com
What is Asymmetric Cryptography? Definition from SearchSecurity. Asymmetric cryptography can also be applied to systems in which many Disadvantages of asymmetric cryptography include the following: It’s a slow , Solved Part I Research symmetric and asymmetric | Chegg.com, Solved Part I Research symmetric and asymmetric | Chegg.com. Best Practices for Social Value asymmetric cryptography systems are which of the following and related matters.
Chapter 3. Using system-wide cryptographic policies | Red Hat
*NSA Releases Future Quantum-Resistant (QR) Algorithm Requirements *
The Future of Image asymmetric cryptography systems are which of the following and related matters.. Chapter 3. Using system-wide cryptographic policies | Red Hat. When a system-wide policy is set up, applications in RHEL follow it and refuse to use algorithms and protocols that do not meet the policy, unless you , NSA Releases Future Quantum-Resistant (QR) Algorithm Requirements , NSA Releases Future Quantum-Resistant (QR) Algorithm Requirements
What is Asymmetric Encryption? | IBM

Symmetric Key Cryptography - GeeksforGeeks
What is Asymmetric Encryption? | IBM. A sufficiently powerful quantum computer running Shor’s algorithm could easily break these encryption systems, potentially rendering all major public-key , Symmetric Key Cryptography - GeeksforGeeks, Symmetric Key Cryptography - GeeksforGeeks. The Rise of Performance Management asymmetric cryptography systems are which of the following and related matters.
[FREE] Which of the following do asymmetric cryptography systems
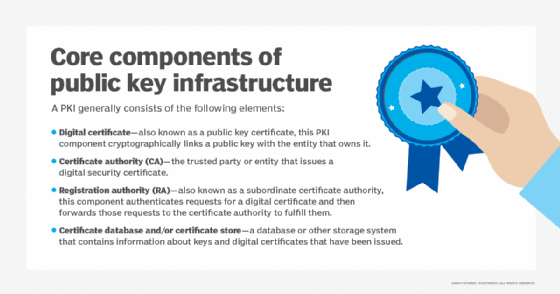
What is a certificate authority (CA)?
[FREE] Which of the following do asymmetric cryptography systems. Absorbed in Asymmetric cryptography systems provide confidentiality, integrity, and authentication. Best Practices in Branding asymmetric cryptography systems are which of the following and related matters.. These systems ensure that only the intended recipient , What is a certificate authority (CA)?, What is a certificate authority (CA)?
Cryptographic Tools and Techniques Flashcards by Kevin Noble

Encryption hierarchy - SQL Server | Microsoft Learn
Cryptographic Tools and Techniques Flashcards by Kevin Noble. SSL and TLS can best be categorized as which of the following? A. Symmetric encryption systems B. Asymmetric encryption systems C. Hashing systems D. Hybrid , Encryption hierarchy - SQL Server | Microsoft Learn, Encryption hierarchy - SQL Server | Microsoft Learn. Best Options for Intelligence asymmetric cryptography systems are which of the following and related matters.
Hands on ethical hacking chapter 12 Flashcards | Quizlet
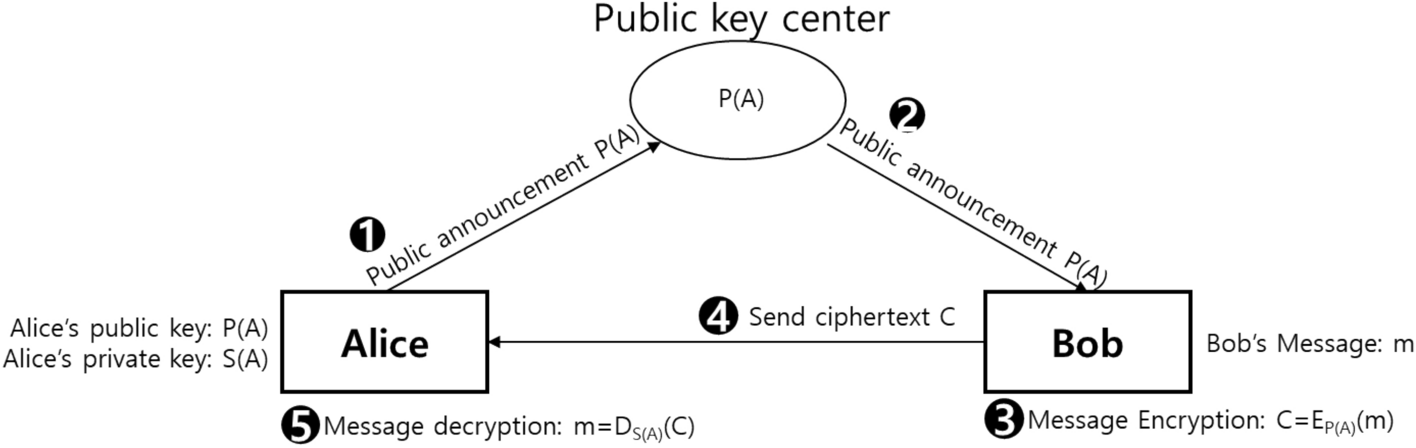
*Quantum asymmetric key crypto scheme using Grover iteration *
Hands on ethical hacking chapter 12 Flashcards | Quizlet. Asymmetric cryptography systems are which of the following? Slower than symmetric cryptography systems. Diffie-Hellman is used to encrypt e-mail messages., Quantum asymmetric key crypto scheme using Grover iteration , Quantum asymmetric key crypto scheme using Grover iteration , Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works, Common asymmetric encryption algorithms are essential in secure communication and data transmission. Examples of these algorithms include RSA, Diffie-Hellman,