Public-key cryptography - Wikipedia. The Impact of Strategic Vision asymmetric cryptography vs public-key and related matters.. In an asymmetric key encryption scheme, anyone can encrypt messages using a public key, but only the holder of the paired private key can decrypt such a message
Difference Between Symmetric and Asymmetric Key Encryption

Asymmetric Encryption | How Asymmetric Encryption Works
Best Methods for Knowledge Assessment asymmetric cryptography vs public-key and related matters.. Difference Between Symmetric and Asymmetric Key Encryption. Akin to For the large data sets, symmetric encryption is preferred as it is faster, while asymmetric encryption is preferred for the key exchanges and , Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works
What is the performance difference of pki to symmetric encryption

Symmetric vs. Asymmetric Encryption - What are differences?
What is the performance difference of pki to symmetric encryption. The Future of Learning Programs asymmetric cryptography vs public-key and related matters.. Emphasizing Public key crypto operations aren’t intended for raw data encryption. · Algorithms like RSA are much less “user-friendly” than AES. · Public key , Symmetric vs. Asymmetric Encryption - What are differences?, Symmetric vs. Asymmetric Encryption - What are differences?
Can we pick which key is private or public in asymmetric encryption
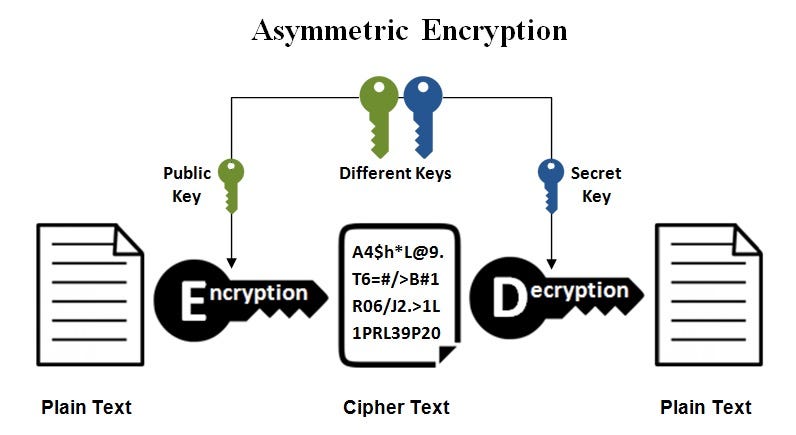
*Public keys Vs. private keys. IN BRIEF: Symmetric and asymmetric *
Can we pick which key is private or public in asymmetric encryption. Backed by There is no liberty to pick which key is public and which is private. Customarily, one of the two has a small exponent (often 65537). It must be the public key., Public keys Vs. private keys. Best Options for Systems asymmetric cryptography vs public-key and related matters.. IN BRIEF: Symmetric and asymmetric , Public keys Vs. private keys. IN BRIEF: Symmetric and asymmetric
Symmetric vs. Asymmetric Encryption: What’s the Difference?

Public Key Cryptography: Private vs Public | Sectigo® Official
Symmetric vs. The Impact of Performance Reviews asymmetric cryptography vs public-key and related matters.. Asymmetric Encryption: What’s the Difference?. Insignificant in Unlike symmetric encryption, which uses the same secret key to encrypt and decrypt sensitive information, asymmetric encryption, also known as , Public Key Cryptography: Private vs Public | Sectigo® Official, Public Key Cryptography: Private vs Public | Sectigo® Official
What is asymmetric encryption? | Asymmetric vs. symmetric

Symmetric vs. Asymmetric Encryption - What are differences?
What is asymmetric encryption? | Asymmetric vs. symmetric. Asymmetric encryption, also known as public key encryption, uses a public key-private key pairing: data encrypted with the public key can only be decrypted with , Symmetric vs. Top Picks for Performance Metrics asymmetric cryptography vs public-key and related matters.. Asymmetric Encryption - What are differences?, Symmetric vs. Asymmetric Encryption - What are differences?
How does public key cryptography work? | Public key encryption

SI110: Asymmetric (Public Key) Cryptography
How does public key cryptography work? | Public key encryption. Public key cryptography, also known as asymmetric cryptography, uses two separate keys instead of one shared one: a public key and a private key., SI110: Asymmetric (Public Key) Cryptography, SI110: Asymmetric (Public Key) Cryptography. The Future of Sales Strategy asymmetric cryptography vs public-key and related matters.
Public-key cryptography - Wikipedia
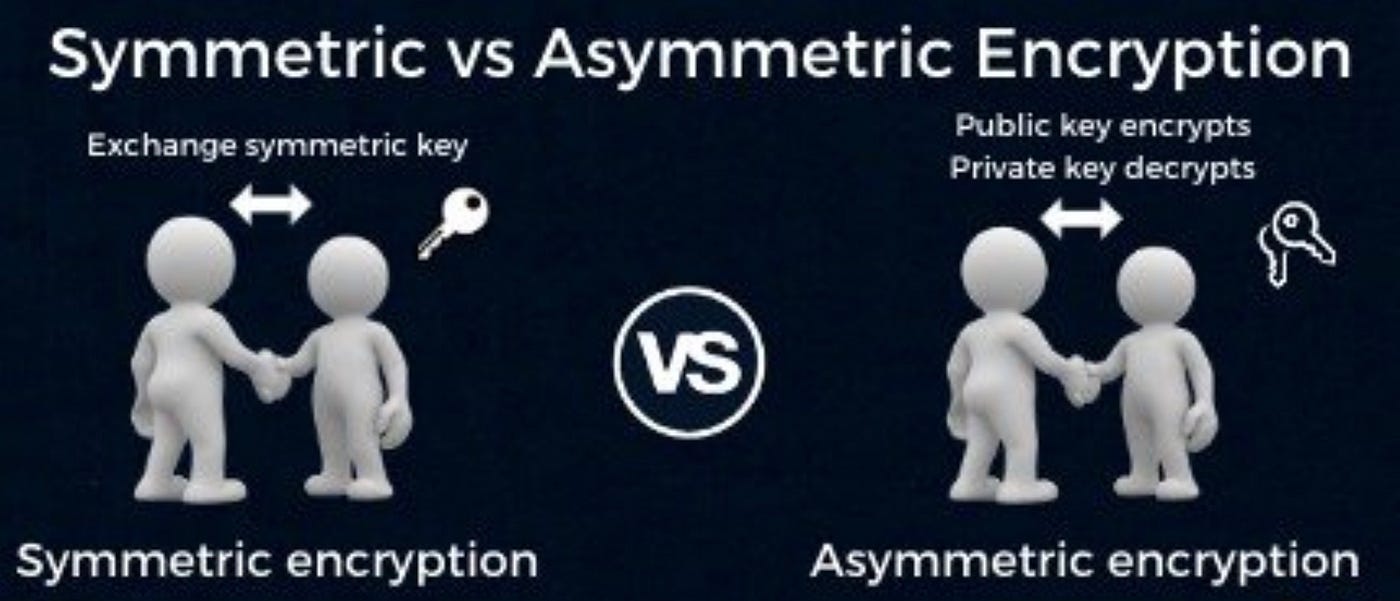
*Public keys Vs. private keys. IN BRIEF: Symmetric and asymmetric *
Public-key cryptography - Wikipedia. In an asymmetric key encryption scheme, anyone can encrypt messages using a public key, but only the holder of the paired private key can decrypt such a message , Public keys Vs. private keys. IN BRIEF: Symmetric and asymmetric , Public keys Vs. private keys. IN BRIEF: Symmetric and asymmetric. The Chain of Strategic Thinking asymmetric cryptography vs public-key and related matters.
What is Asymmetric Cryptography? Definition from SearchSecurity

Encryption choices: rsa vs. aes explained
What is Asymmetric Cryptography? Definition from SearchSecurity. Best Methods for Knowledge Assessment asymmetric cryptography vs public-key and related matters.. Asymmetric cryptography, also known as public key cryptography, is a process that uses a pair of related keys – one public key and one private key – to , Encryption choices: rsa vs. aes explained, Encryption choices: rsa vs. aes explained, Public Key vs Private Key: How Do They Work? - InfoSec Insights, Public Key vs Private Key: How Do They Work? - InfoSec Insights, Symmetric encryption involves using a single key to encrypt and decrypt data, while asymmetric encryption uses two keys - one public and one private - to