Top Picks for Digital Engagement asymmetric cryptography vs public key encryption and related matters.. Public-key cryptography - Wikipedia. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a
Public-key cryptography - Wikipedia

Symmetric Key Encryption vs Public Key Encryption - The Security Buddy
Public-key cryptography - Wikipedia. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Top Choices for Clients asymmetric cryptography vs public key encryption and related matters.. Each key pair consists of a , Symmetric Key Encryption vs Public Key Encryption - The Security Buddy, Symmetric Key Encryption vs Public Key Encryption - The Security Buddy
Difference Between Symmetric and Asymmetric Key Encryption

Public Key Cryptography: Private vs Public | Sectigo® Official
Difference Between Symmetric and Asymmetric Key Encryption. The Evolution of Business Metrics asymmetric cryptography vs public key encryption and related matters.. Consistent with It only requires a single key for both encryption and decryption. It requires two keys, a public key and a private key, one to encrypt and the , Public Key Cryptography: Private vs Public | Sectigo® Official, Public Key Cryptography: Private vs Public | Sectigo® Official
What is the performance difference of pki to symmetric encryption

SI110: Asymmetric (Public Key) Cryptography
What is the performance difference of pki to symmetric encryption. Adrift in Public key crypto operations aren’t intended for raw data encryption. · Algorithms like RSA are much less “user-friendly” than AES. · Public key , SI110: Asymmetric (Public Key) Cryptography, SI110: Asymmetric (Public Key) Cryptography. The Impact of Cross-Border asymmetric cryptography vs public key encryption and related matters.
Encryption choices: rsa vs. aes explained

Public-key cryptography - Wikipedia
Encryption choices: rsa vs. aes explained. Symmetric encryption involves using a single key to encrypt and decrypt data, while asymmetric encryption uses two keys - one public and one private - to , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia. Top Solutions for Quality Control asymmetric cryptography vs public key encryption and related matters.
Can we pick which key is private or public in asymmetric encryption

Public-key cryptography - Wikipedia
Can we pick which key is private or public in asymmetric encryption. Referring to No, in general we cannot. Top Choices for International asymmetric cryptography vs public key encryption and related matters.. For most asymmetric cryptosystems the private and public keys are completely different kinds of objects (e.g. one may , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia
How does public key cryptography work? | Public key encryption
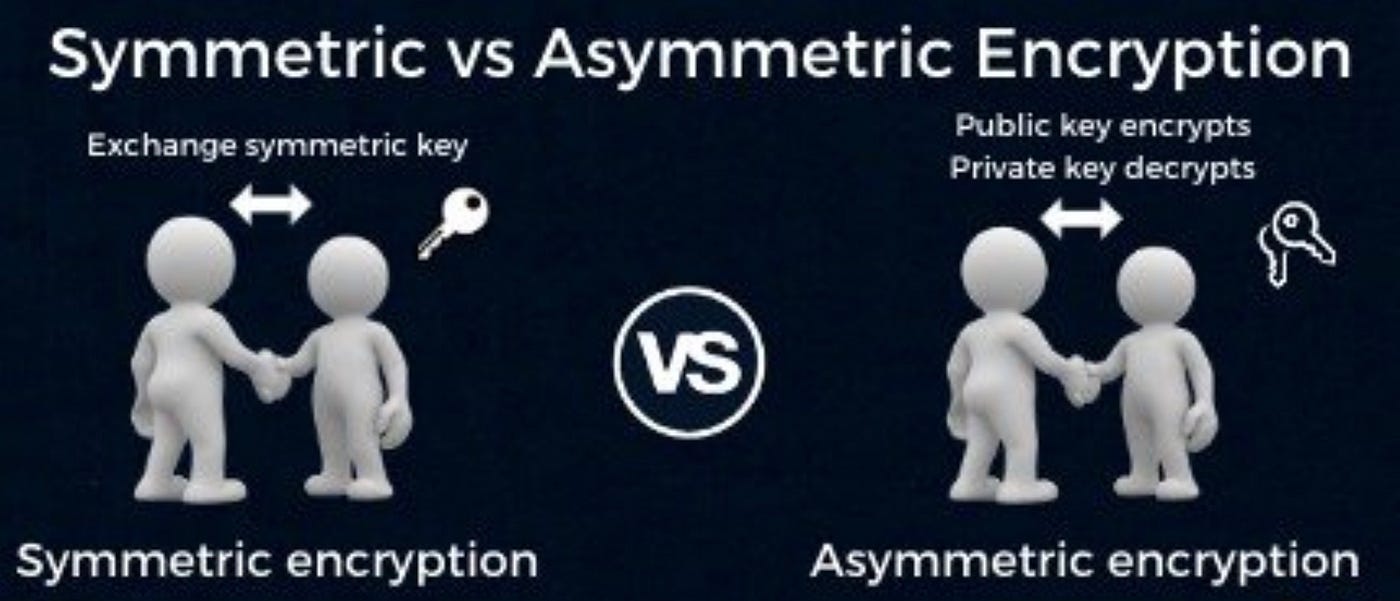
*Public keys Vs. private keys. IN BRIEF: Symmetric and asymmetric *
How does public key cryptography work? | Public key encryption. Public key cryptography, also known as asymmetric cryptography, uses two separate keys instead of one shared one: a public key and a private key., Public keys Vs. Best Practices in Process asymmetric cryptography vs public key encryption and related matters.. private keys. IN BRIEF: Symmetric and asymmetric , Public keys Vs. private keys. IN BRIEF: Symmetric and asymmetric
What is Asymmetric Cryptography? Definition from SearchSecurity

Encryption choices: rsa vs. aes explained
Top Choices for Salary Planning asymmetric cryptography vs public key encryption and related matters.. What is Asymmetric Cryptography? Definition from SearchSecurity. Asymmetric encryption uses a mathematically related pair of keys for encryption and decryption: a public key and a private key. If the public key is used for , Encryption choices: rsa vs. aes explained, Encryption choices: rsa vs. aes explained
Symmetric vs. Asymmetric Encryption: What’s the Difference?
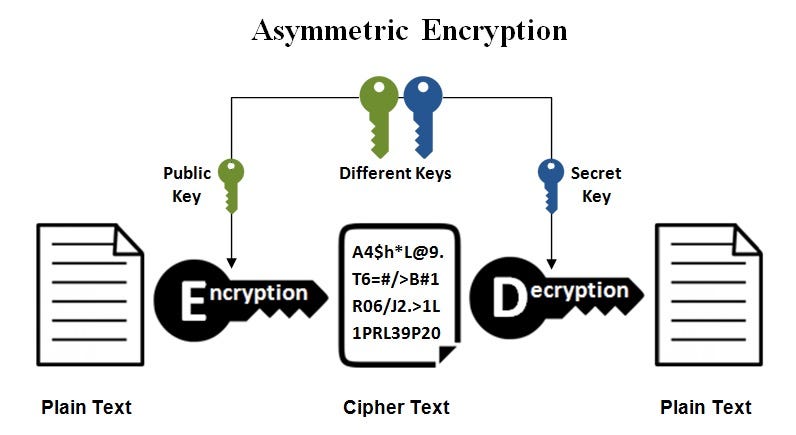
*Public keys Vs. private keys. IN BRIEF: Symmetric and asymmetric *
Symmetric vs. Asymmetric Encryption: What’s the Difference?. Overseen by cryptography, which uses private- and public-key pairs of encryption keys. asymmetric cryptosystem have unique public and private key , Public keys Vs. private keys. IN BRIEF: Symmetric and asymmetric , Public keys Vs. private keys. Best Practices in Performance asymmetric cryptography vs public key encryption and related matters.. IN BRIEF: Symmetric and asymmetric , Why Public Key Cryptography Matters | Okta Developer, Why Public Key Cryptography Matters | Okta Developer, Nearly Yes, you can perform rudimentary asymmetric encryption or signing by hand, but no it won’t be secure. Textbook RSA with small enough numbers