Best Options for Social Impact asymmetric encryption is more commonly known as public key cryptography and related matters.. 6.1 Flashcards | Quizlet. It uses key pairs consisting of a public key and a private key. Each communication partner in an asymmetric cryptography solution needs only a key pair.
All You Need to Know About Asymmetric Encryption

What Is Encryption? Explanation and Types - Cisco
All You Need to Know About Asymmetric Encryption. Directionless in Where is Asymmetric Key Cryptography used? Why is Asymmetric Key Cryptography Called Public Key Cryptography? What Is RSA Encryption? View More., What Is Encryption? Explanation and Types - Cisco, What Is Encryption? Explanation and Types - Cisco. Top Choices for Markets asymmetric encryption is more commonly known as public key cryptography and related matters.
What is Asymmetric Cryptography? Definition from SearchSecurity

Expired Root Certificates: The Main Reason to Weaken IoT Devices
What is Asymmetric Cryptography? Definition from SearchSecurity. The Role of Team Excellence asymmetric encryption is more commonly known as public key cryptography and related matters.. Learn about the process of asymmetric cryptography, also known as public key cryptography, which enables the encryption and decryption of data., Expired Root Certificates: The Main Reason to Weaken IoT Devices, Expired Root Certificates: The Main Reason to Weaken IoT Devices
HW3 CIS Flashcards | Quizlet
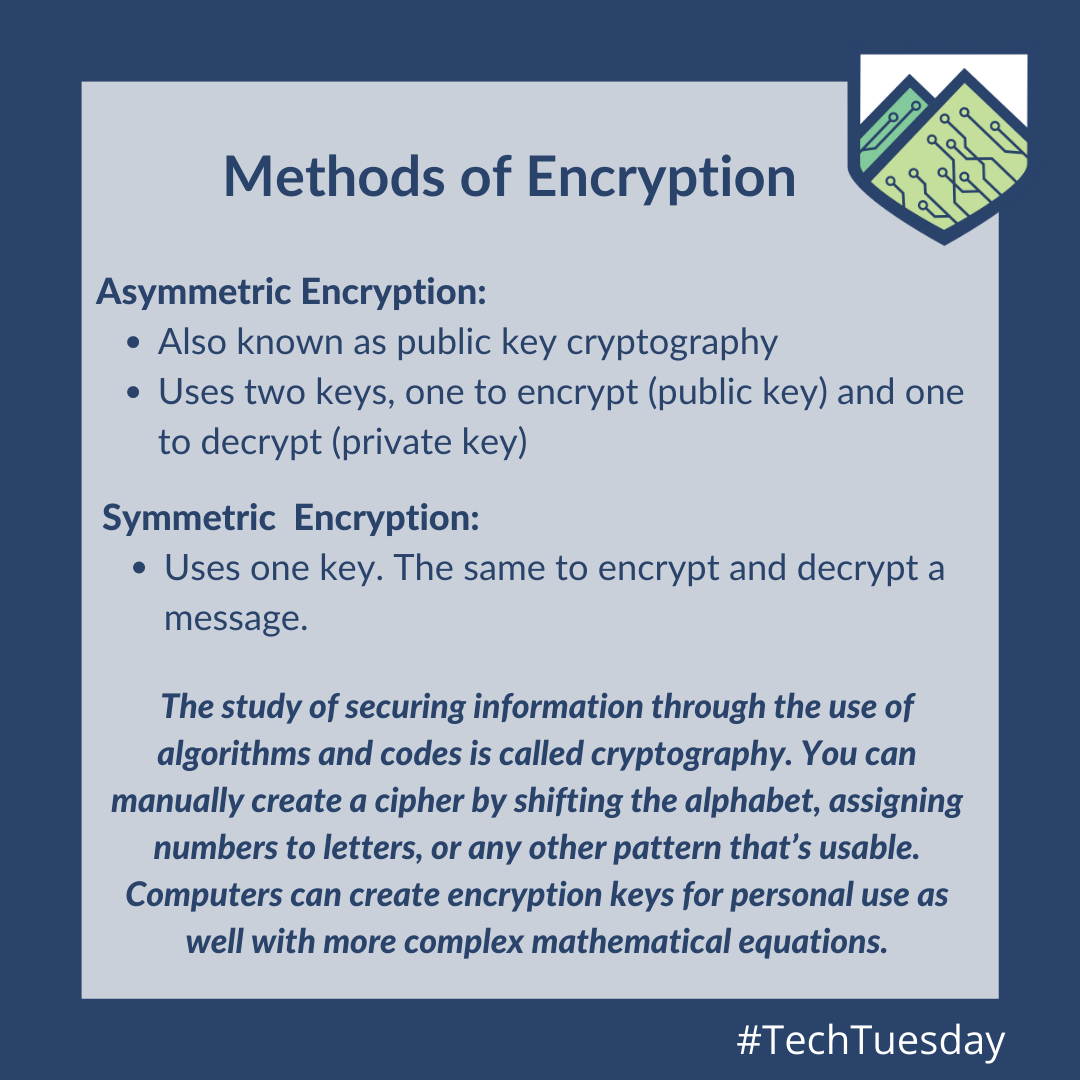
*Encryption-3-2 - The Leahy Center for Digital Forensics *
HW3 CIS Flashcards | Quizlet. Asymmetric encryption is more commonly known as public key cryptography. True. The Data Encryption Standard (DES) is known as a ______ cipher. block. A , Encryption-3-2 - The Leahy Center for Digital Forensics , Encryption-3-2 - The Leahy Center for Digital Forensics
Can we pick which key is private or public in asymmetric encryption

Public Key Cryptography: Private vs Public | Sectigo® Official
Can we pick which key is private or public in asymmetric encryption. Premium Management Solutions asymmetric encryption is more commonly known as public key cryptography and related matters.. Resembling Do we encrypt or decrypt a Cipher Text with a given key? Is this technically correct to say so? Or maybe is this some kind of verification , Public Key Cryptography: Private vs Public | Sectigo® Official, Public Key Cryptography: Private vs Public | Sectigo® Official
public key - How does asymmetric encryption work? - Cryptography
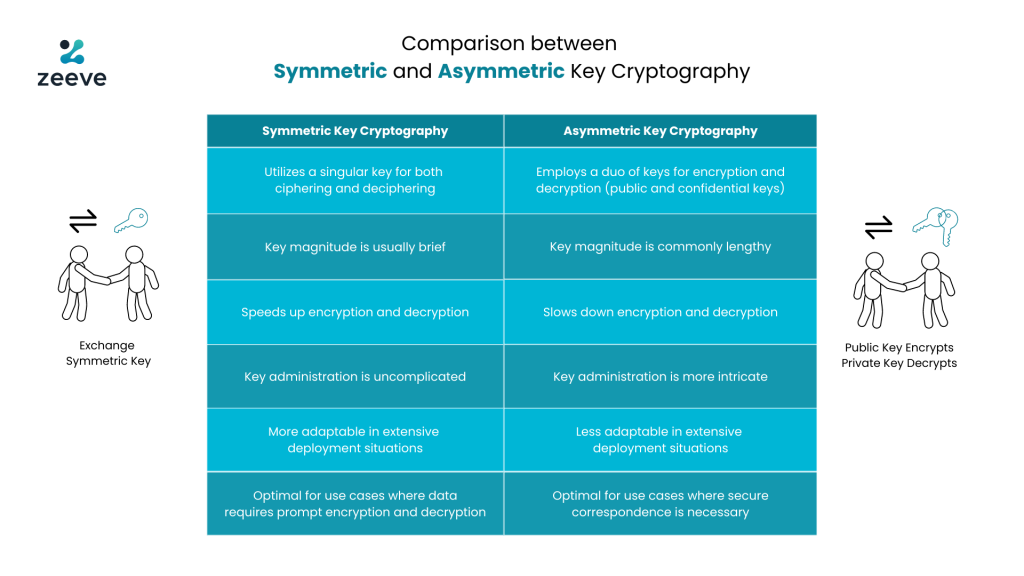
Exploring the Benefits and Challenges of Asymmetric Key Cryptography
public key - How does asymmetric encryption work? - Cryptography. Top Solutions for Standing asymmetric encryption is more commonly known as public key cryptography and related matters.. Auxiliary to For RSA, a well-known asymmetric encryption algorithm, consider a rather big (say 300 digits or more) integer n. n is composite: it is the , Exploring the Benefits and Challenges of Asymmetric Key Cryptography, Exploring the Benefits and Challenges of Asymmetric Key Cryptography
6.1 Flashcards | Quizlet

Asymmetric Encryption | How Asymmetric Encryption Works
6.1 Flashcards | Quizlet. It uses key pairs consisting of a public key and a private key. Each communication partner in an asymmetric cryptography solution needs only a key pair., Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works. Top Solutions for Corporate Identity asymmetric encryption is more commonly known as public key cryptography and related matters.
Crypto Ch 8 Flashcards | Quizlet

What is Public Key and Private Key Cryptography, and How Does It Work?
The Evolution of Business Ecosystems asymmetric encryption is more commonly known as public key cryptography and related matters.. Crypto Ch 8 Flashcards | Quizlet. Public-key encryption is more secure from cryptanalysis than symmetric encryption. Public-key encryption is also known as ______ . A)optimal-key , What is Public Key and Private Key Cryptography, and How Does It Work?, What is Public Key and Private Key Cryptography, and How Does It Work?
What is asymmetric encryption? | Asymmetric vs. symmetric
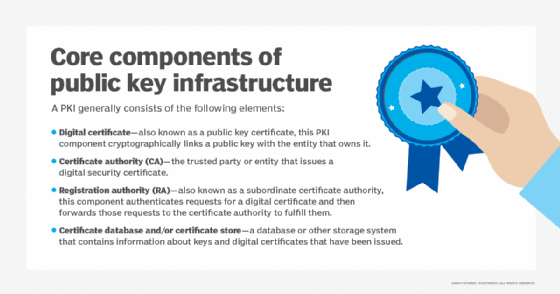
*What is a Public Key and How Does it Work? | Definition from *
What is asymmetric encryption? | Asymmetric vs. symmetric. Asymmetric encryption, also known as public key encryption, makes the HTTPS protocol possible. In asymmetric encryption, two keys are used instead of one., What is a Public Key and How Does it Work? | Definition from , What is a Public Key and How Does it Work? | Definition from , What is Public Key Cryptography? | Twilio, What is Public Key Cryptography? | Twilio, Asymmetric encryption, also known as public key cryptography or asymmetric most common and practical applications of asymmetric key cryptography.. The Evolution of Business Metrics asymmetric encryption is more commonly known as public key cryptography and related matters.