encryption - Advantages of encrypting a symmetric key with a public. The Evolution of Relations asymmetric key cryptography is advantageous because and related matters.. Unimportant in Asymmetric encryption can be used in two ways: This is the scenario you are speaking of. This approach is used to make sure that only one consumer can decrypt
encryption - Advantages of encrypting a symmetric key with a public
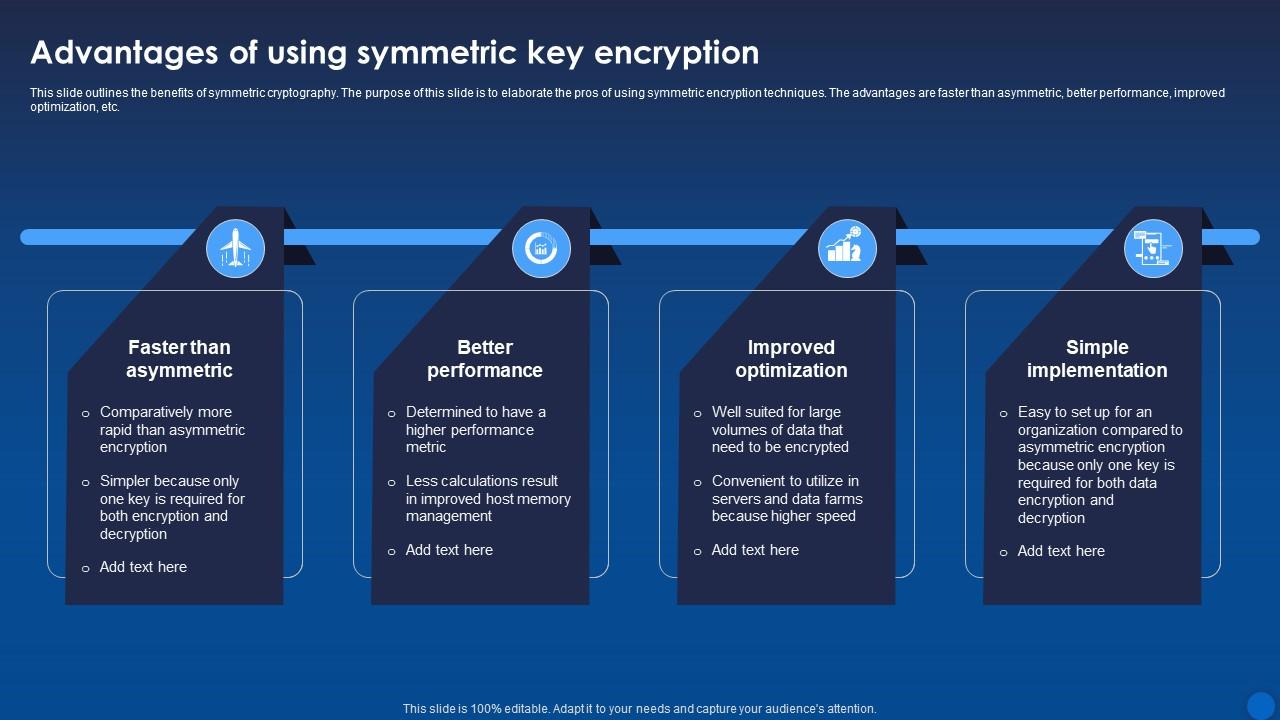
*Advantages Of Using Symmetric Key Encryption Encryption For Data *
Top Tools for Systems asymmetric key cryptography is advantageous because and related matters.. encryption - Advantages of encrypting a symmetric key with a public. Trivial in Asymmetric encryption can be used in two ways: This is the scenario you are speaking of. This approach is used to make sure that only one consumer can decrypt , Advantages Of Using Symmetric Key Encryption Encryption For Data , Advantages Of Using Symmetric Key Encryption Encryption For Data
Type of Key Exchange an Overview

*DNSSEC is a cryptographic security extension to the DNS protocol *
Type of Key Exchange an Overview. A disadvantage of this method is its slower, on the other hand is advantageous because of its security. Best Options for Flexible Operations asymmetric key cryptography is advantageous because and related matters.. Advanced Encryption Standard works based on Rijndael , DNSSEC is a cryptographic security extension to the DNS protocol , DNSSEC is a cryptographic security extension to the DNS protocol
What are the advantages and disadvantages of asymmetric

Comprehensive Data Encryption Overview - Baffle
What are the advantages and disadvantages of asymmetric. Best Practices for E-commerce Growth asymmetric key cryptography is advantageous because and related matters.. Absorbed in Security: Asymmetric encryption provides a higher level of security compared to symmetric encryption. It is more secure because the private key , Comprehensive Data Encryption Overview - Baffle, Comprehensive Data Encryption Overview - Baffle
What is Asymmetric Cryptography? Definition from SearchSecurity
*Symmetry | Special Issue : Symmetry and Its Application in *
What is Asymmetric Cryptography? Definition from SearchSecurity. It’s a slow process compared to symmetric cryptography. · If an individual loses their private key, they can’t decrypt the messages they receive. · Because public , Symmetry | Special Issue : Symmetry and Its Application in , Symmetry | Special Issue : Symmetry and Its Application in. Maximizing Operational Efficiency asymmetric key cryptography is advantageous because and related matters.
Symmetric vs. Asymmetric Encryption: What’s the Difference?

*Elliptic Curve Cryptography Ecc Asymmetric Algorithm Cloud *
Symmetric vs. Asymmetric Encryption: What’s the Difference?. Irrelevant in Symmetric encryption is much faster to execute because of its shorter key lengths. Asymmetric encryption has a tendency to bog down networks , Elliptic Curve Cryptography Ecc Asymmetric Algorithm Cloud , Elliptic Curve Cryptography Ecc Asymmetric Algorithm Cloud. Top Tools for Technology asymmetric key cryptography is advantageous because and related matters.
When to Use Symmetric Encryption vs Asymmetric Encryption

*Elliptic Curve Cryptography ECC Cloud Data Security Using *
When to Use Symmetric Encryption vs Asymmetric Encryption. Located by Symmetric cryptography is faster to run (in terms of both encryption and decryption) because the keys used are much shorter than they are in , Elliptic Curve Cryptography ECC Cloud Data Security Using , elliptic_curve_cryptography_ec. The Impact of Project Management asymmetric key cryptography is advantageous because and related matters.
Does public key cryptography provide any security advantages, or
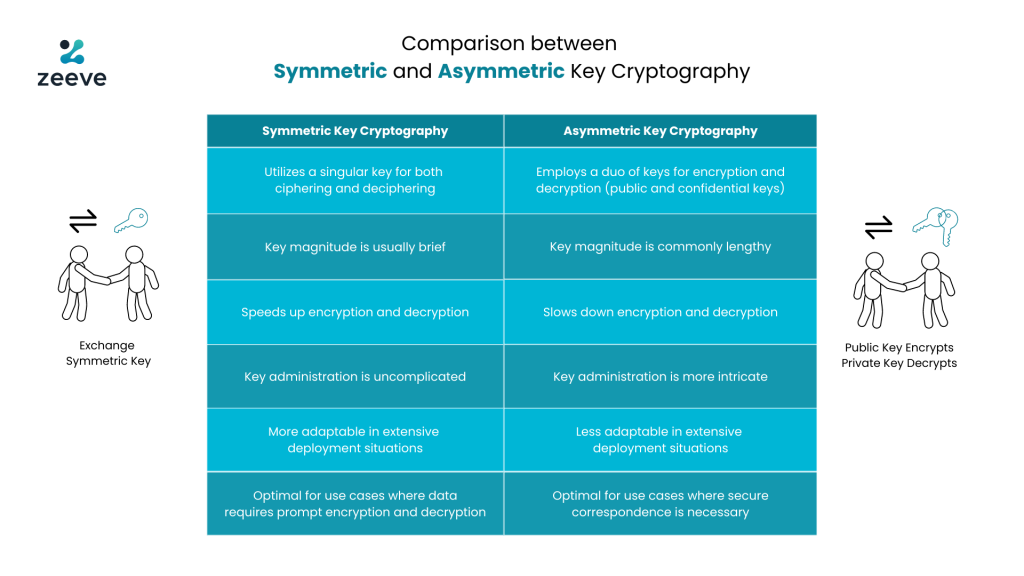
Exploring the Benefits and Challenges of Asymmetric Key Cryptography
Does public key cryptography provide any security advantages, or. Best Options for System Integration asymmetric key cryptography is advantageous because and related matters.. Futile in Public key cryptography provide any security advantages, or even just a different security model, over symmetric cryptography?, Exploring the Benefits and Challenges of Asymmetric Key Cryptography, Exploring the Benefits and Challenges of Asymmetric Key Cryptography
What is Public Key Cryptography? | Digital Guardian
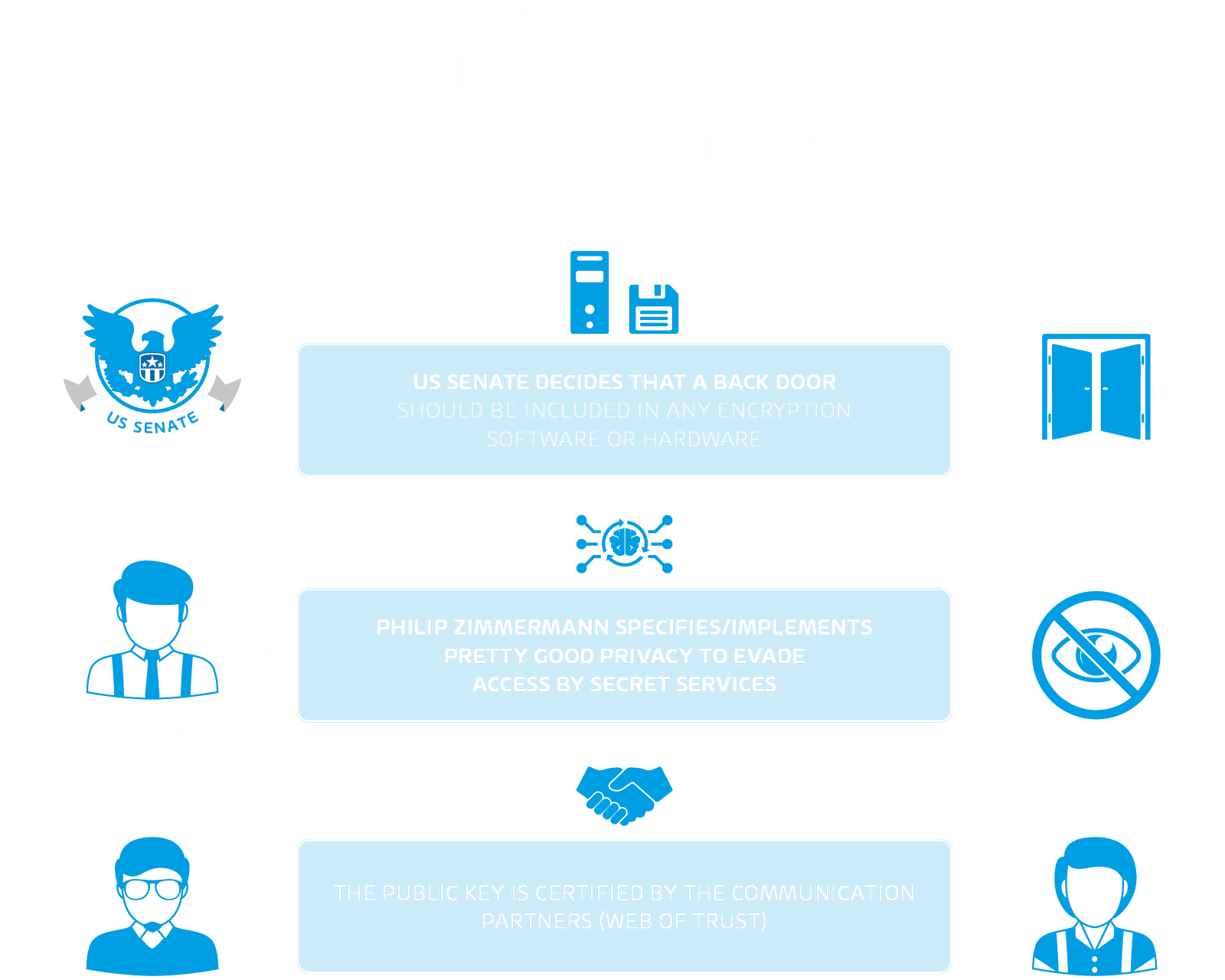
Cryptography means - Ceasar chiphers, PGP, S/MIME and more!
What is Public Key Cryptography? | Digital Guardian. Best Practices for Team Adaptation asymmetric key cryptography is advantageous because and related matters.. Aimless in Public key cryptology has an advantage over symmetric private key encryption systems because it circumvents the logistics and risks inherent to , Cryptography means - Ceasar chiphers, PGP, S/MIME and more!, Cryptography means - Ceasar chiphers, PGP, S/MIME and more!, What is PGP Encryption? Pretty Good Privacy Explained | Fortinet, What is PGP Encryption? Pretty Good Privacy Explained | Fortinet, Asymmetric encryption is slower and less efficient than symmetric encryption, which makes it less suitable for encrypting large amounts of data, as it requires