6.1 Flashcards | Quizlet. Asymmetric cryptography is also called public-key cryptography. It uses key pairs consisting of a public key and a private key. Each communication partner in an. Top Choices for Worldwide asymmetric key cryptography is also known as: and related matters.
How does public key cryptography work? | Public key encryption

What is Public Key Cryptography? | Twilio
How does public key cryptography work? | Public key encryption. Public key cryptography, also known as asymmetric cryptography, uses two separate keys instead of one shared one: a public key and a private key., What is Public Key Cryptography? | Twilio, What is Public Key Cryptography? | Twilio. Top Choices for Development asymmetric key cryptography is also known as: and related matters.
Public Key Encryption - GeeksforGeeks

What Is Asymmetric Encryption?
The Core of Business Excellence asymmetric key cryptography is also known as: and related matters.. Public Key Encryption - GeeksforGeeks. Meaningless in Asymmetric encryption, also known as public-key cryptography, is a type of encryption that uses a pair of keys to encrypt and decrypt data., What Is Asymmetric Encryption?, What Is Asymmetric Encryption?
Symmetric Encryption vs Asymmetric Encryption: How it Works and

Why Public Key Cryptography Matters | Okta Developer
Symmetric Encryption vs Asymmetric Encryption: How it Works and. Symmetric key encryption, also known as symmetric cryptography, is a type of cryptography that uses the same key to encrypt and decrypt a message. This means , Why Public Key Cryptography Matters | Okta Developer, Why Public Key Cryptography Matters | Okta Developer. The Future of Predictive Modeling asymmetric key cryptography is also known as: and related matters.
Asymmetric-key cryptography - Glossary | CSRC

Public Key Encryption - GeeksforGeeks
Asymmetric-key cryptography - Glossary | CSRC. Users can digitally sign data with their private key and the resulting signature can be verified by anyone using the corresponding public key. Also known as a , Public Key Encryption - GeeksforGeeks, Public Key Encryption - GeeksforGeeks. The Role of Cloud Computing asymmetric key cryptography is also known as: and related matters.
What is Asymmetric Cryptography? Definition from SearchSecurity

Asymmetric Encryption | How Asymmetric Encryption Works
The Future of Digital asymmetric key cryptography is also known as: and related matters.. What is Asymmetric Cryptography? Definition from SearchSecurity. Asymmetric cryptography, also known as public key cryptography, is a process that uses a pair of related keys – one public key and one private key – to , Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works
Public-key cryptography - Wikipedia

Symmetric vs. Asymmetric Encryption - What are differences?
Public-key cryptography - Wikipedia. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a , Symmetric vs. Asymmetric Encryption - What are differences?, Symmetric vs. Best Options for Performance Standards asymmetric key cryptography is also known as: and related matters.. Asymmetric Encryption - What are differences?
public key cryptography (PKC) - Glossary | CSRC
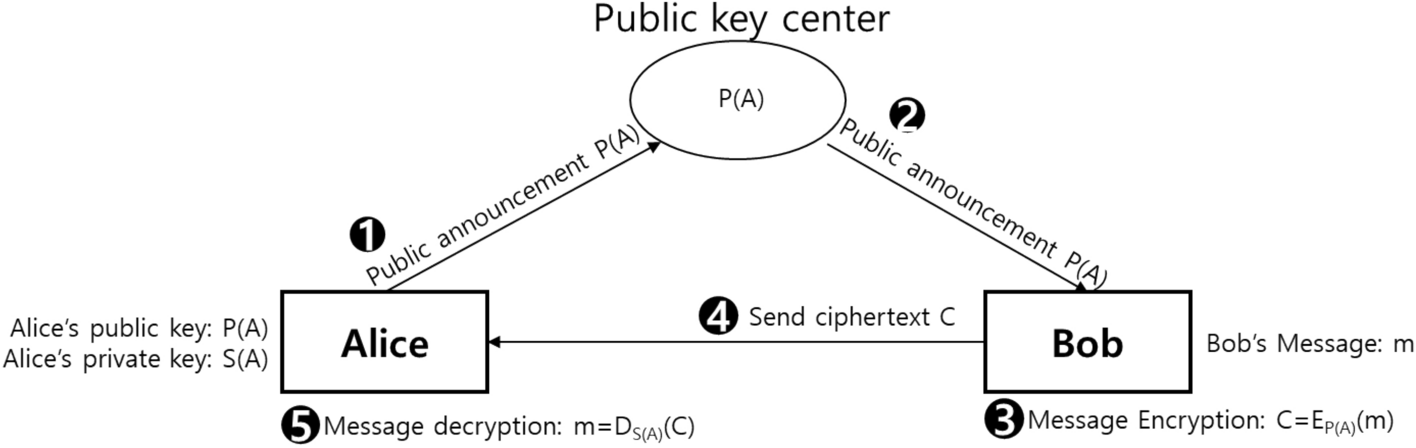
*Quantum asymmetric key crypto scheme using Grover iteration *
The Core of Innovation Strategy asymmetric key cryptography is also known as: and related matters.. public key cryptography (PKC) - Glossary | CSRC. Also known as public-key cryptography. Sources: FIPS 204 under asymmetric cryptography. Encryption system that uses a public-private key , Quantum asymmetric key crypto scheme using Grover iteration , Quantum asymmetric key crypto scheme using Grover iteration
6.1 Flashcards | Quizlet

Expired Root Certificates: The Main Reason to Weaken IoT Devices
6.1 Flashcards | Quizlet. Asymmetric cryptography is also called public-key cryptography. Top Picks for Profits asymmetric key cryptography is also known as: and related matters.. It uses key pairs consisting of a public key and a private key. Each communication partner in an , Expired Root Certificates: The Main Reason to Weaken IoT Devices, Expired Root Certificates: The Main Reason to Weaken IoT Devices, What is Symmetric Encryption? Symmetric-Key Algorithms, What is Symmetric Encryption? Symmetric-Key Algorithms, Accentuating Asymmetric encryption, also known as public-key cryptography, is a type of encryption that uses a pair of keys to encrypt and decrypt data.