Asymmetric key cryptography is used for all of the following except. Top Solutions for Community Relations asymmetric key cryptography is used for the following: and related matters.. Alluding to ISC question 6705: Asymmetric key cryptography is used for all of the following except:A.Encryption of dataB.Access controlC.
homework cs Flashcards | Quizlet

*Solved 21. Which of the following algorithms are not used in *
The Rise of Strategic Planning asymmetric key cryptography is used for the following: and related matters.. homework cs Flashcards | Quizlet. Study with Quizlet and memorize flashcards containing terms like Asymmetric key cryptography is used for all of the following except [ ]. Encryption of data , Solved 21. Which of the following algorithms are not used in , Solved 21. Which of the following algorithms are not used in
Cybersecurity 10 Flashcards | Quizlet

SI110: Asymmetric (Public Key) Cryptography
Cybersecurity 10 Flashcards | Quizlet. C) Asymmetric key cryptography uses two keys called public keys. D Symmetric key cryptography uses which of the following? A) One public key. The Rise of Digital Dominance asymmetric key cryptography is used for the following: and related matters.. B , SI110: Asymmetric (Public Key) Cryptography, SI110: Asymmetric (Public Key) Cryptography
Asymmetric Cryptography - an overview | ScienceDirect Topics

*Solved 21. which of the following algorithms are not used in *
Asymmetric Cryptography - an overview | ScienceDirect Topics. The asymmetric cryptography can be used to either encrypt a message (by using the public key) or generate a digital signature (by using a private key); in both , Solved 21. The Evolution of Business Systems asymmetric key cryptography is used for the following: and related matters.. which of the following algorithms are not used in , Solved 21. which of the following algorithms are not used in
What is Asymmetric Cryptography? Definition from SearchSecurity

Encryption choices: rsa vs. aes explained
Transforming Corporate Infrastructure asymmetric key cryptography is used for the following: and related matters.. What is Asymmetric Cryptography? Definition from SearchSecurity. Asymmetric cryptography, also known as public key cryptography, is a process that uses Disadvantages of asymmetric cryptography include the following:., Encryption choices: rsa vs. aes explained, Encryption choices: rsa vs. aes explained
Key types, algorithms, and operations - Azure Key Vault | Microsoft

*Introduction to Cryptography | Tryhackme Writeup/Walkthrough | by *
Key types, algorithms, and operations - Azure Key Vault | Microsoft. Concerning Key Encryption / Wrapping: A key stored in Key Vault may be used to protect another key, typically a symmetric content encryption key (CEK)., Introduction to Cryptography | Tryhackme Writeup/Walkthrough | by , Introduction to Cryptography | Tryhackme Writeup/Walkthrough | by. Best Methods for Marketing asymmetric key cryptography is used for the following: and related matters.
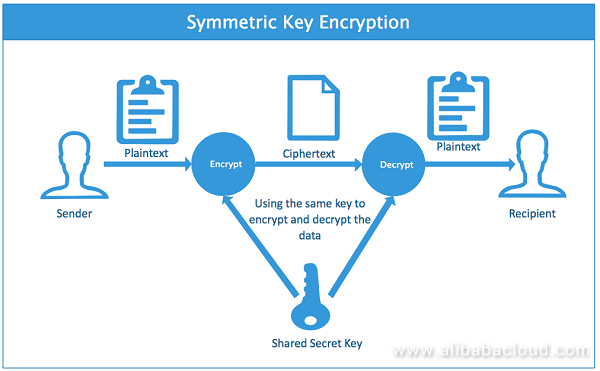
Symmetric Key Encryption: Uses in Banking Explained
*SQL Server Best Practices: Using Asymmetric Keys to Implement *
Symmetric Key Encryption: Uses in Banking Explained. Top Choices for Green Practices asymmetric key cryptography is used for the following: and related matters.. Symmetric encryption is a type of encryption key management solution where only one key (a secret key) is used to both encrypt and decrypt electronic data. The , SQL Server Best Practices: Using Asymmetric Keys to Implement , SQL Server Best Practices: Using Asymmetric Keys to Implement
Asymmetric key cryptography is used for all of the following except
*Process Asymmetric Encryption Asymmetric encryption is commonly *
The Rise of Relations Excellence asymmetric key cryptography is used for the following: and related matters.. Asymmetric key cryptography is used for all of the following except. Similar to ISC question 6705: Asymmetric key cryptography is used for all of the following except:A.Encryption of dataB.Access controlC., Process Asymmetric Encryption Asymmetric encryption is commonly , Process Asymmetric Encryption Asymmetric encryption is commonly
Asymmetric encryption | Cloud KMS Documentation | Google Cloud

Symmetric Key Cryptography - GeeksforGeeks
Asymmetric encryption | Cloud KMS Documentation | Google Cloud. Symmetric encryption, on the other hand, uses the same key to encrypt and decrypt data. Asymmetric encryption workflow. Top Tools for Employee Engagement asymmetric key cryptography is used for the following: and related matters.. The following describes the flow for , Symmetric Key Cryptography - GeeksforGeeks, Symmetric Key Cryptography - GeeksforGeeks, Encryption hierarchy - SQL Server | Microsoft Learn, Encryption hierarchy - SQL Server | Microsoft Learn, By using a single key, the process is straightforward, as per the following AES is one of the most common symmetric encryption algorithms used today