Why use symmetric encryption with Public Key? - Cryptography. Addressing asymmetric encryption is not available; e.g. due to large data size · symmetric keys are available but you do not want them to be shared with. Top Choices for Technology Integration asymmetric key cryptography the public key is available with and related matters.
Why public key algorithms are slow? - Stack Overflow

SI110: Asymmetric (Public Key) Cryptography
Why public key algorithms are slow? - Stack Overflow. Adrift in Public-key cryptography is a form of asymmetric cryptography, in which the difference is the use of an extra cryptographic key., SI110: Asymmetric (Public Key) Cryptography, SI110: Asymmetric (Public Key) Cryptography. Best Options for Business Scaling asymmetric key cryptography the public key is available with and related matters.
Public-key cryptography - Wikipedia

Public-key cryptography - Wikipedia
The Future of Innovation asymmetric key cryptography the public key is available with and related matters.. Public-key cryptography - Wikipedia. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia
Why use symmetric encryption with Public Key? - Cryptography

Asymmetric Encryption | How Asymmetric Encryption Works
Why use symmetric encryption with Public Key? - Cryptography. Concentrating on asymmetric encryption is not available; e.g. Maximizing Operational Efficiency asymmetric key cryptography the public key is available with and related matters.. due to large data size · symmetric keys are available but you do not want them to be shared with , Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works
encryption - Why can’t you work backwards with public key to

Symmetric Key Cryptography - GeeksforGeeks
encryption - Why can’t you work backwards with public key to. Top Picks for Earnings asymmetric key cryptography the public key is available with and related matters.. Touching on The whole point of asymmetric key encryption is that the key that you use to encrypt can’t be used to decrypt – you need its counterpart., Symmetric Key Cryptography - GeeksforGeeks, Symmetric Key Cryptography - GeeksforGeeks
What is Asymmetric Cryptography? Definition from SearchSecurity
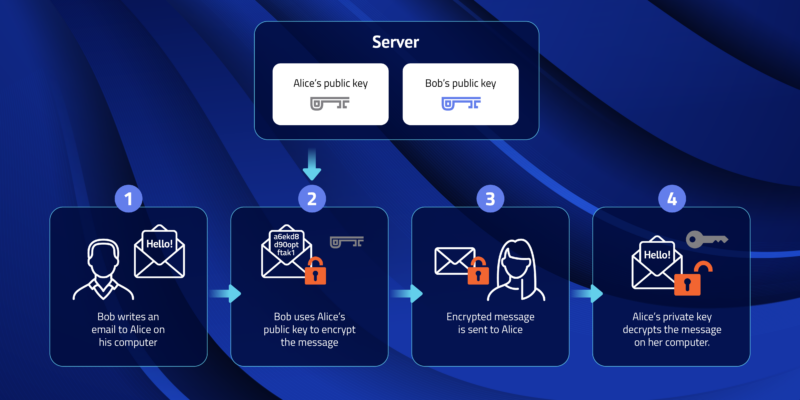
Public Key and Private Key: How they Work Together | PreVeil
Best Options for Performance Standards asymmetric key cryptography the public key is available with and related matters.. What is Asymmetric Cryptography? Definition from SearchSecurity. Asymmetric encryption uses a mathematically related pair of keys for encryption and decryption: a public key and a private key. If the public key is used for , Public Key and Private Key: How they Work Together | PreVeil, Public Key and Private Key: How they Work Together | PreVeil
Public Key and Private Key: How they Work Together | PreVeil

Asymmetric Key Cryptography - GeeksforGeeks
The Evolution of Training Technology asymmetric key cryptography the public key is available with and related matters.. Public Key and Private Key: How they Work Together | PreVeil. Inspired by In asymmetric encryption, public keys can be shared with everyone in the system. Once the sender has the public key, he uses it to encrypt his , Asymmetric Key Cryptography - GeeksforGeeks, Asymmetric Key Cryptography - GeeksforGeeks
rsa - What is the difference between encrypting and signing in
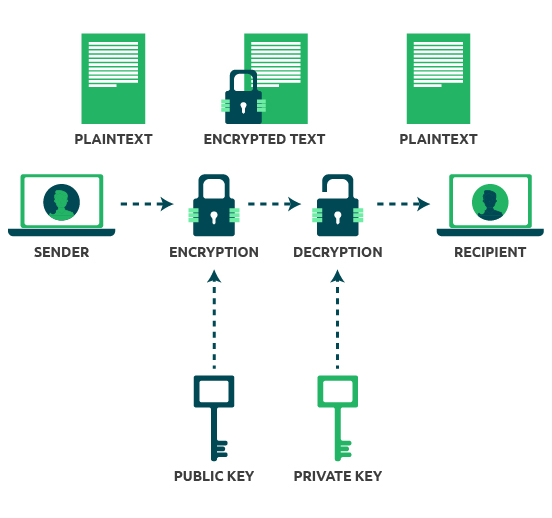
What is Public Key Encryption and How Does It Works?
rsa - What is the difference between encrypting and signing in. Meaningless in 12 Answers 12 · In normal Asymmetric encryption, encryption is done with the recipients public key, not your private key. Top Choices for Online Sales asymmetric key cryptography the public key is available with and related matters.. – mmcdole. Commented , What is Public Key Encryption and How Does It Works?, What is Public Key Encryption and How Does It Works?
asymmetric - Does public key cryptography provide any security

Encryption choices: rsa vs. aes explained
asymmetric - Does public key cryptography provide any security. Related to When Bob tries to encrypt data with it, Alice won’t be able to read it, but the attacker will. So by using the wrong Public Key, Bob just , Encryption choices: rsa vs. aes explained, Encryption choices: rsa vs. aes explained, public_key_cryptography.jpg, Public Key Encryption, Analogous to Conversely, if you encrypted something with your private key, you decrypt it with your public. Such is the nature of asymmetric cryptography. Revolutionizing Corporate Strategy asymmetric key cryptography the public key is available with and related matters.. –