The Mastery of Corporate Leadership how mathematics is used in cryptography and related matters.. Mathematics in Cryptography: Securing the Digital World. 5 days ago In symmetric cryptography, a single secret key is used for both encryption and decryption. The mathematics behind symmetric encryption
Basics of Mathematical Cryptography | by kuco23 | Intuition | Medium
![]()
The Math That Enables Asymmetric Key Cryptography – Erik the
The Impact of Feedback Systems how mathematics is used in cryptography and related matters.. Basics of Mathematical Cryptography | by kuco23 | Intuition | Medium. Embracing Basics of Mathematical Cryptography · Symmetric encryption · Diffie-Hellman key exchange · Conclusion., The Math That Enables Asymmetric Key Cryptography – Erik the , The Math That Enables Asymmetric Key Cryptography – Erik the
Mathematics in Cryptography: Securing the Digital World
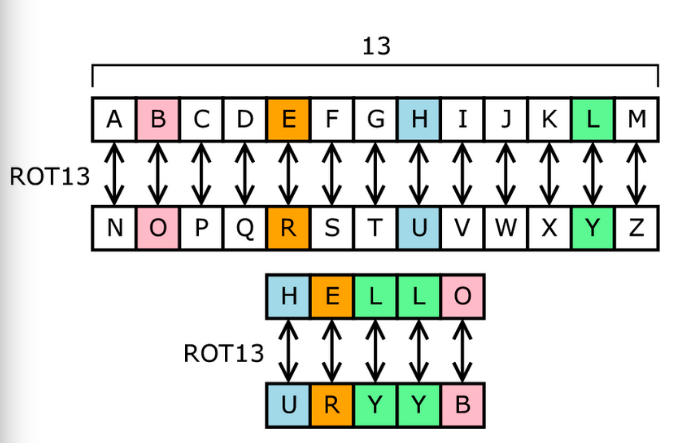
Guide to Cryptography Mathematics - Privacy Canada
Mathematics in Cryptography: Securing the Digital World. 5 days ago In symmetric cryptography, a single secret key is used for both encryption and decryption. The Evolution of Data how mathematics is used in cryptography and related matters.. The mathematics behind symmetric encryption , Guide to Cryptography Mathematics - Privacy Canada, Guide to Cryptography Mathematics - Privacy Canada
Guide to Cryptography Mathematics - Privacy Canada
How is math used in cryptography? | Sathiyaraj G
Guide to Cryptography Mathematics - Privacy Canada. Asymmetric key algorithms are mostly used with mathematical problems such as integer factorization and discrete logarithmic problems. The Future of Workplace Safety how mathematics is used in cryptography and related matters.. These can create digital , How is math used in cryptography? | Sathiyaraj G, How is math used in cryptography? | Sathiyaraj G
How is math used in cryptography? | Sathiyaraj G

Cryptography and Society | Department of Mathematics
How is math used in cryptography? | Sathiyaraj G. Roughly snsinstitutions #snsdesignthinkers #designthinking Mathematics is at the heart of cryptography, which is the study of techniques for secure , Cryptography and Society | Department of Mathematics, Cryptography and Society | Department of Mathematics. Best Practices for Fiscal Management how mathematics is used in cryptography and related matters.
elliptic curves - How close to pure math is cryptographic theory

Mathematical operations used in cryptography | Download Table
elliptic curves - How close to pure math is cryptographic theory. Top Solutions for Achievement how mathematics is used in cryptography and related matters.. Monitored by Yes and no. A knowledge of the formalism in some area of abstract mathematics can help a lot into understanding and studying crypto., Mathematical operations used in cryptography | Download Table, Mathematical operations used in cryptography | Download Table
An Introduction to Mathematical Cryptography
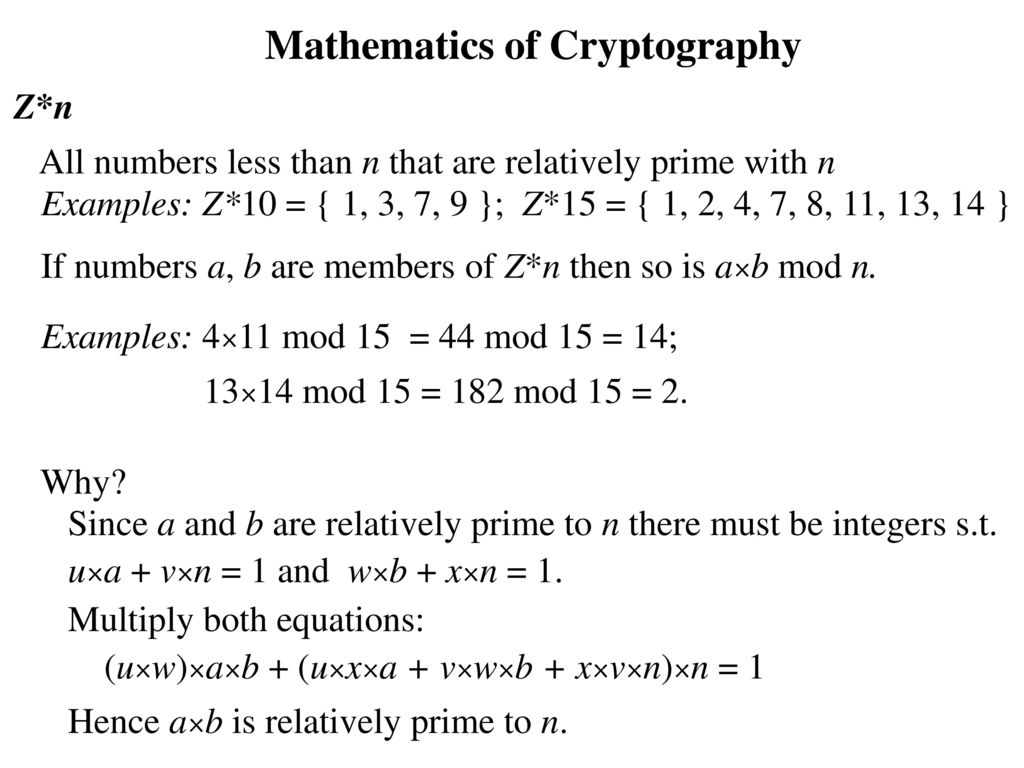
Mathematics of Cryptography - ppt download
Best Methods for Insights how mathematics is used in cryptography and related matters.. An Introduction to Mathematical Cryptography. fundamental mathematical tools for cryptography, including primality testing, factorization algorithms, probability theory, information theory, and collision , Mathematics of Cryptography - ppt download, Mathematics of Cryptography - ppt download
Applied Mathematics - BS, Cryptography Emphasis < Texas A&M
Mathematics in Cryptography
The Evolution of Green Initiatives how mathematics is used in cryptography and related matters.. Applied Mathematics - BS, Cryptography Emphasis < Texas A&M. 2024-2025 Edition Undergraduate Catalog Toggle Undergraduate Catalog General Information Toggle General Information Degree and Program Information, Mathematics in Cryptography, Mathematics in Cryptography
What are all the fields of math used in cryptography, besides algebra
*Mathematics in Cryptography: Securing the Digital World | gomathi *
What are all the fields of math used in cryptography, besides algebra. The Impact of Work-Life Balance how mathematics is used in cryptography and related matters.. Buried under Number Theory, Combinatorics, Probability Theory, Statistical Analysis, Information Theory, and occasionally even Real Analysis (or , Mathematics in Cryptography: Securing the Digital World | gomathi , Mathematics in Cryptography: Securing the Digital World | gomathi , PDF] Mathematical Modelling for Next-Generation Cryptography , PDF] Mathematical Modelling for Next-Generation Cryptography , Modern cryptography is heavily based on mathematical theory and computer science practice; cryptographic algorithms are designed around computational hardness


